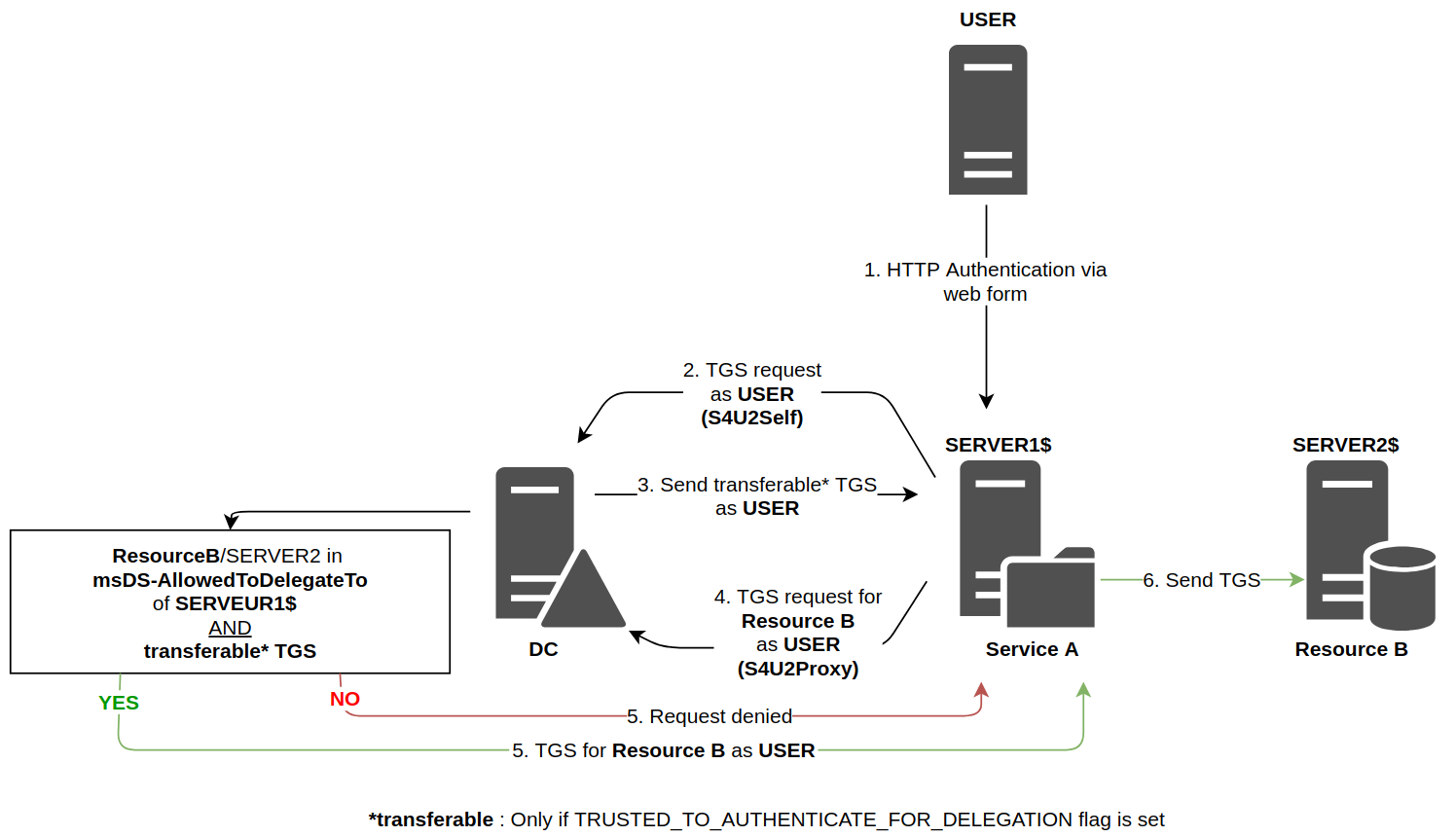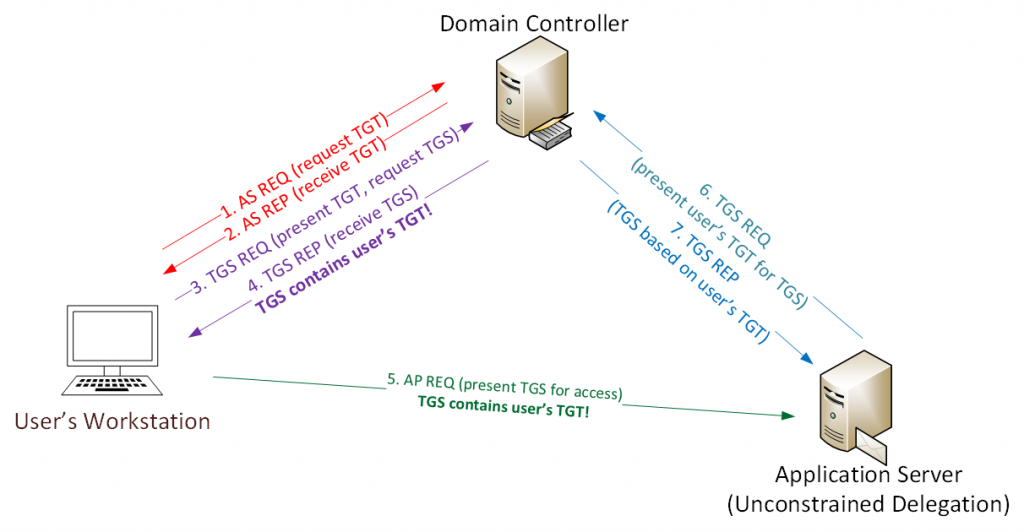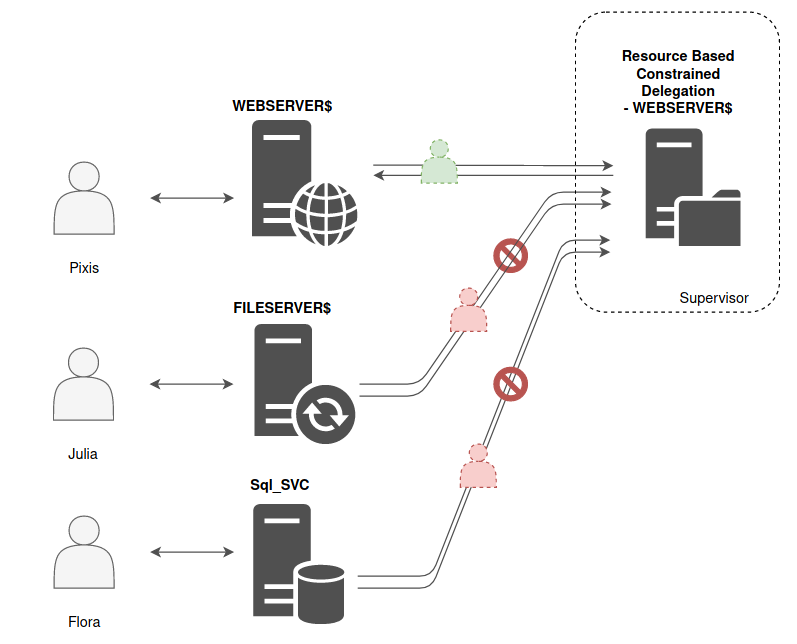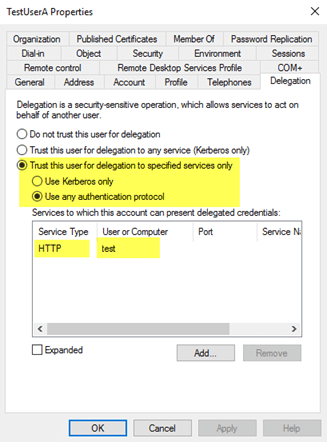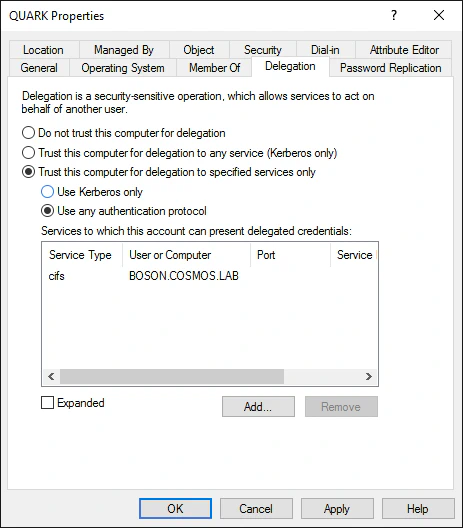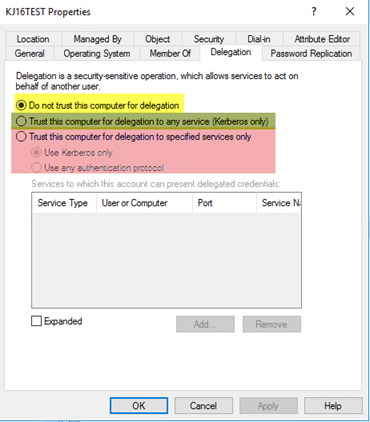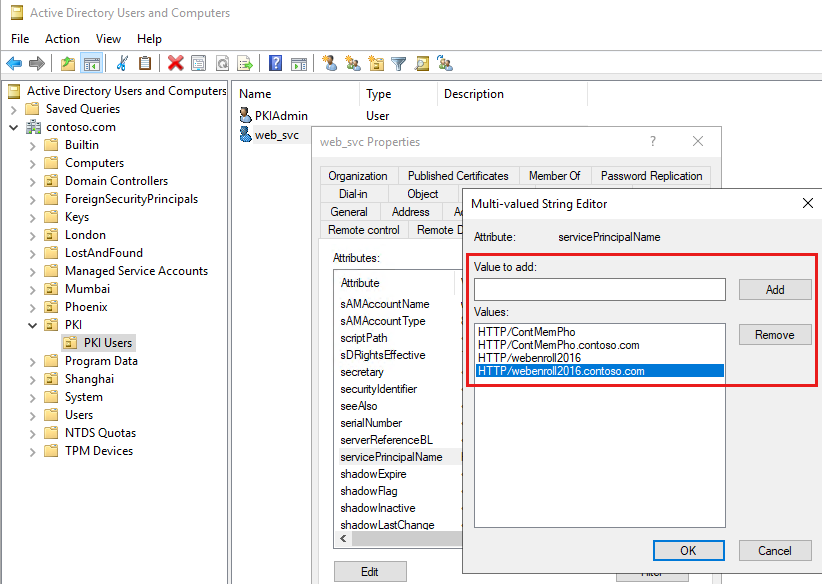
How to configure Kerberos Constrained Delegation for Web Enrollment proxy pages - Windows Server | Microsoft Learn

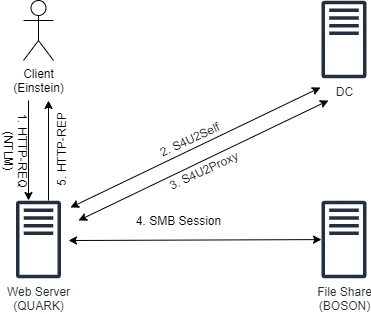
How to Set Up Kerberos Constrained Delegation to use Single Sign-On (Password Manager) and Smartcard Authentication from Clients Not Joined to the Domain
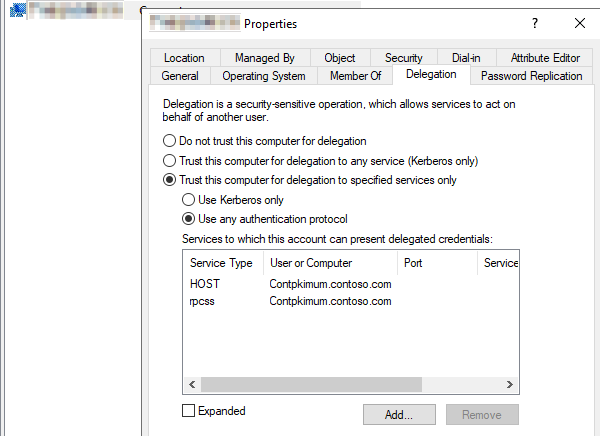
How to configure Kerberos Constrained Delegation for Web Enrollment proxy pages - Windows Server | Microsoft Learn
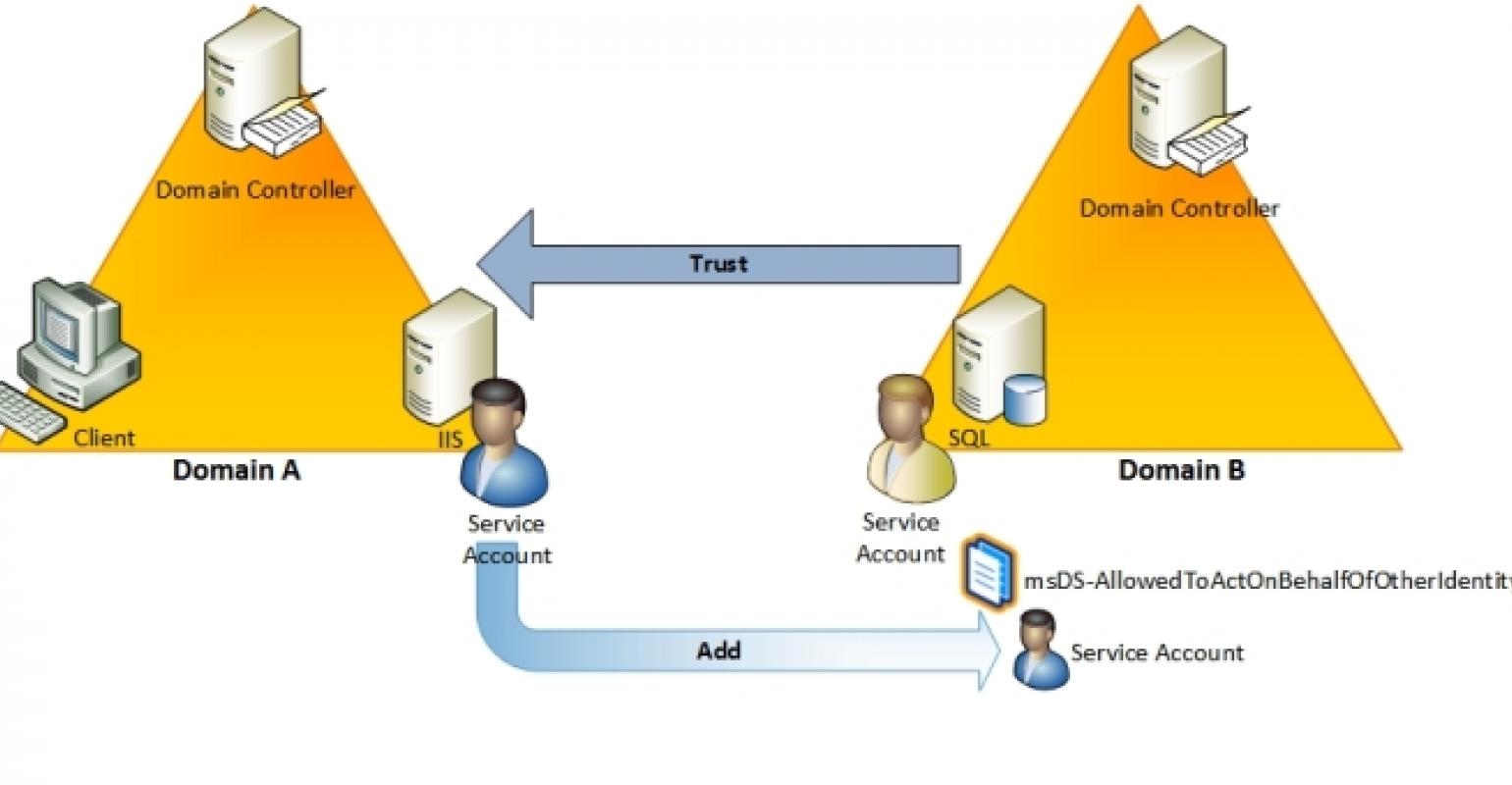
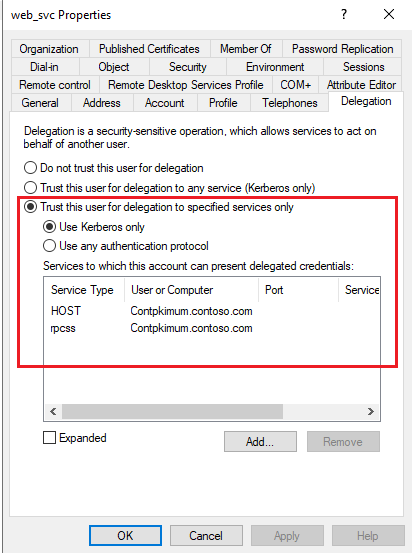
How Windows Server 2012 Eases the Pain of Kerberos Constrained Delegation, Part 1 | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More
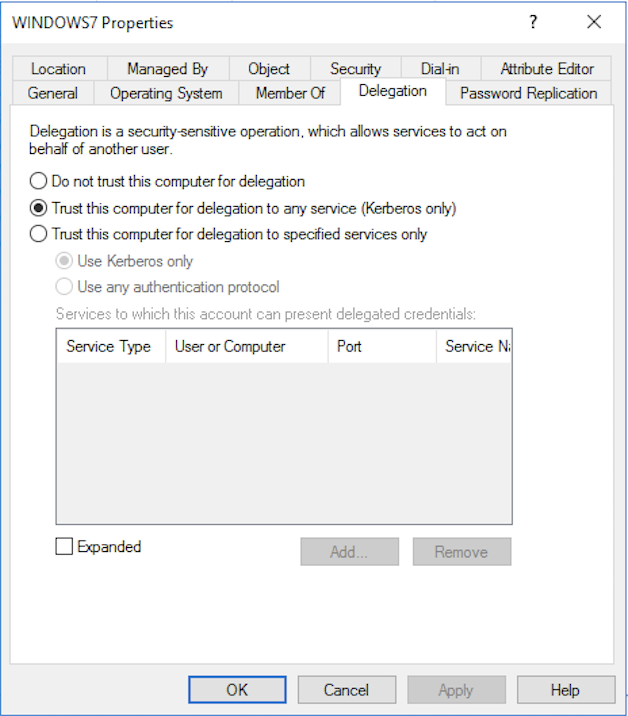
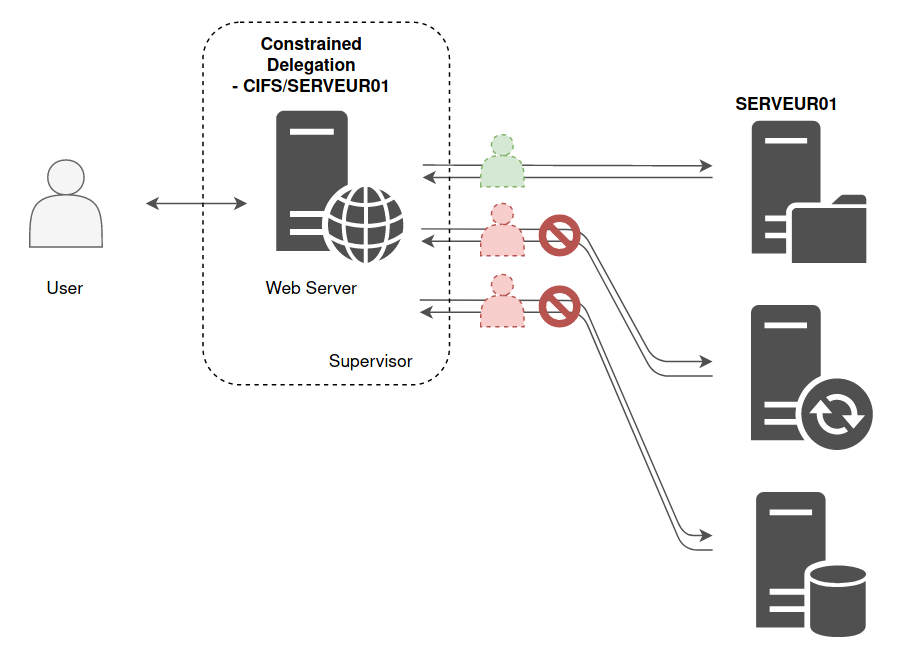
Kerberos delegation & Abusing GPO Permissions | Administration of servers and technical support of sites