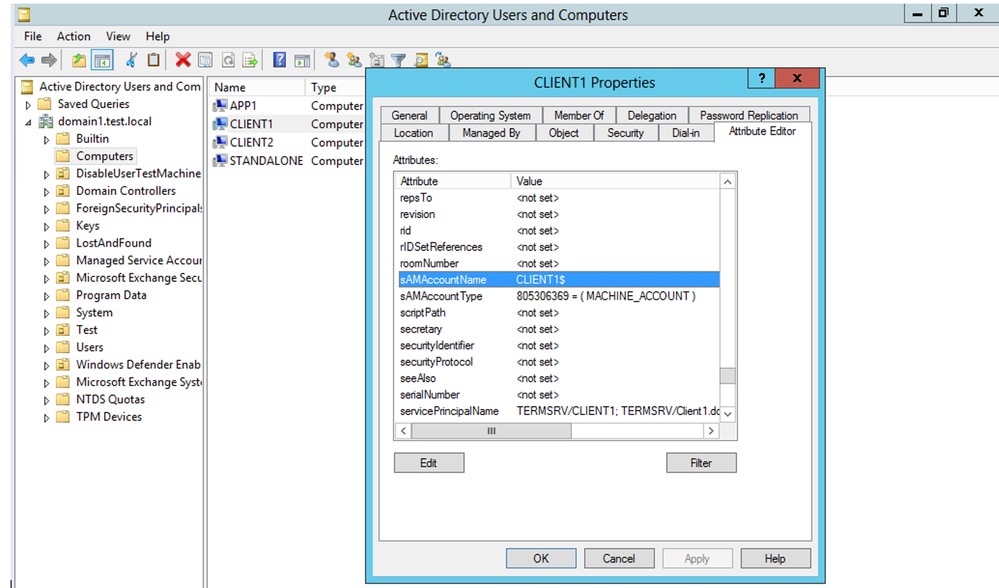
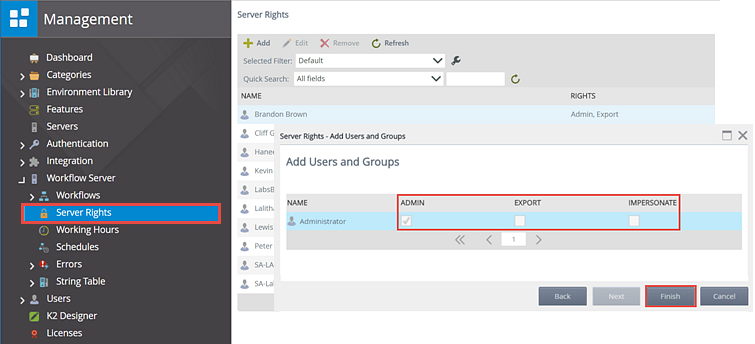
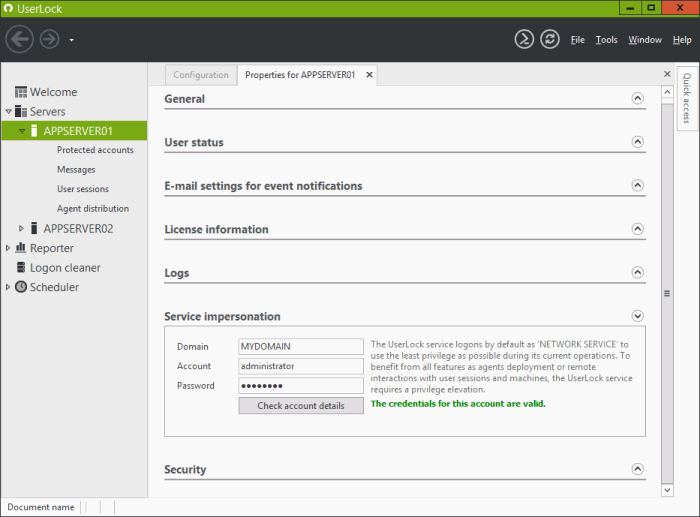
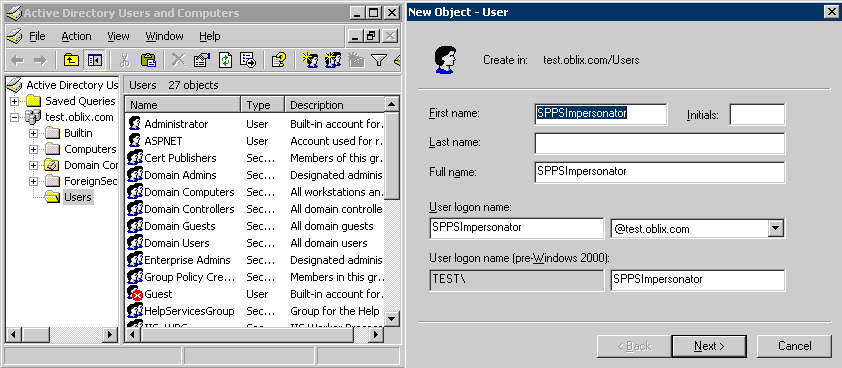
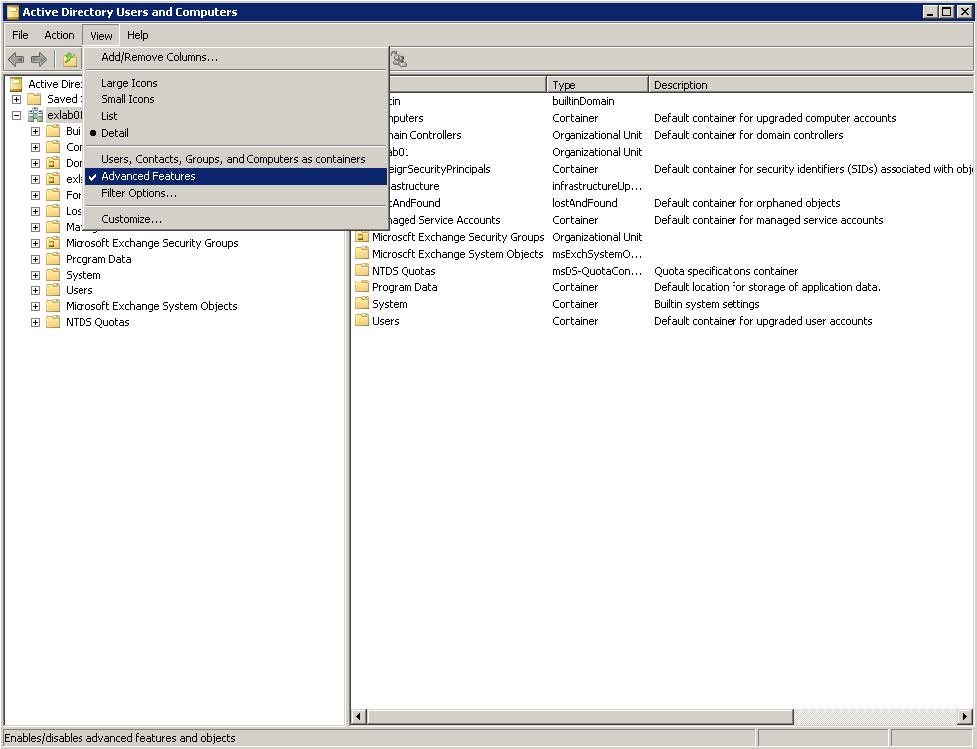
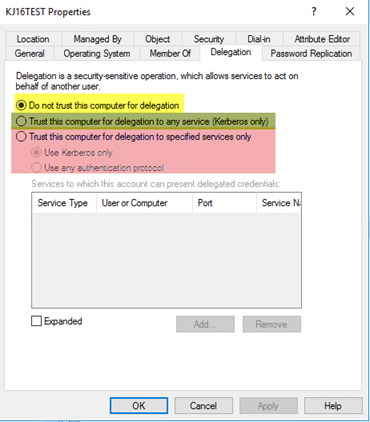
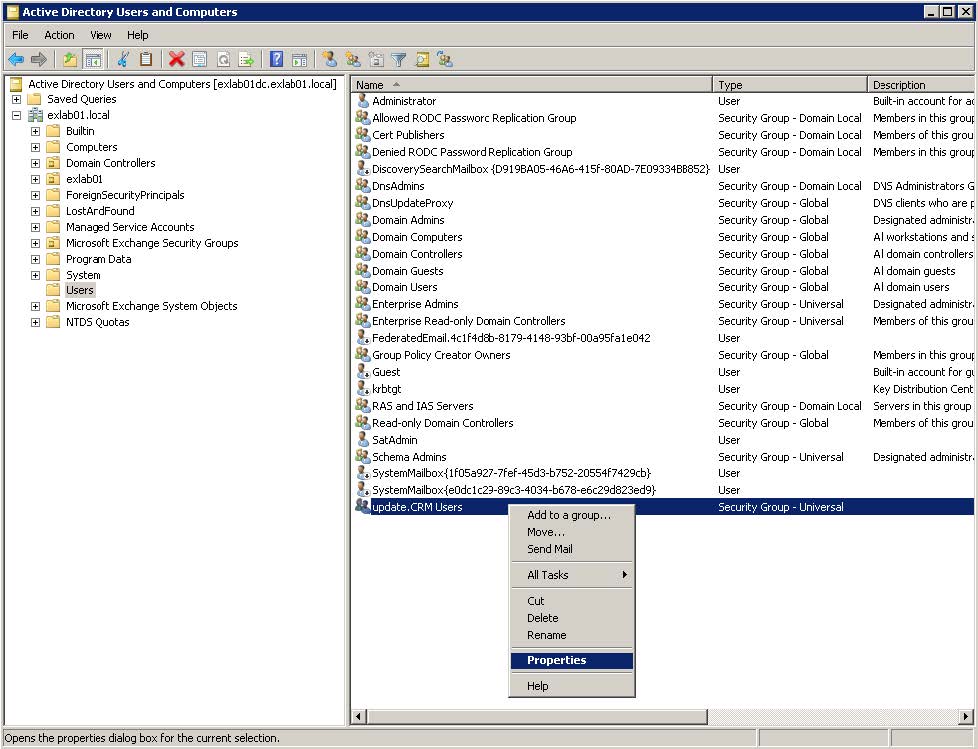
Token impersonation | Active Directory | Windows Privilege Escalation | Cyber Security for Beginners - YouTube
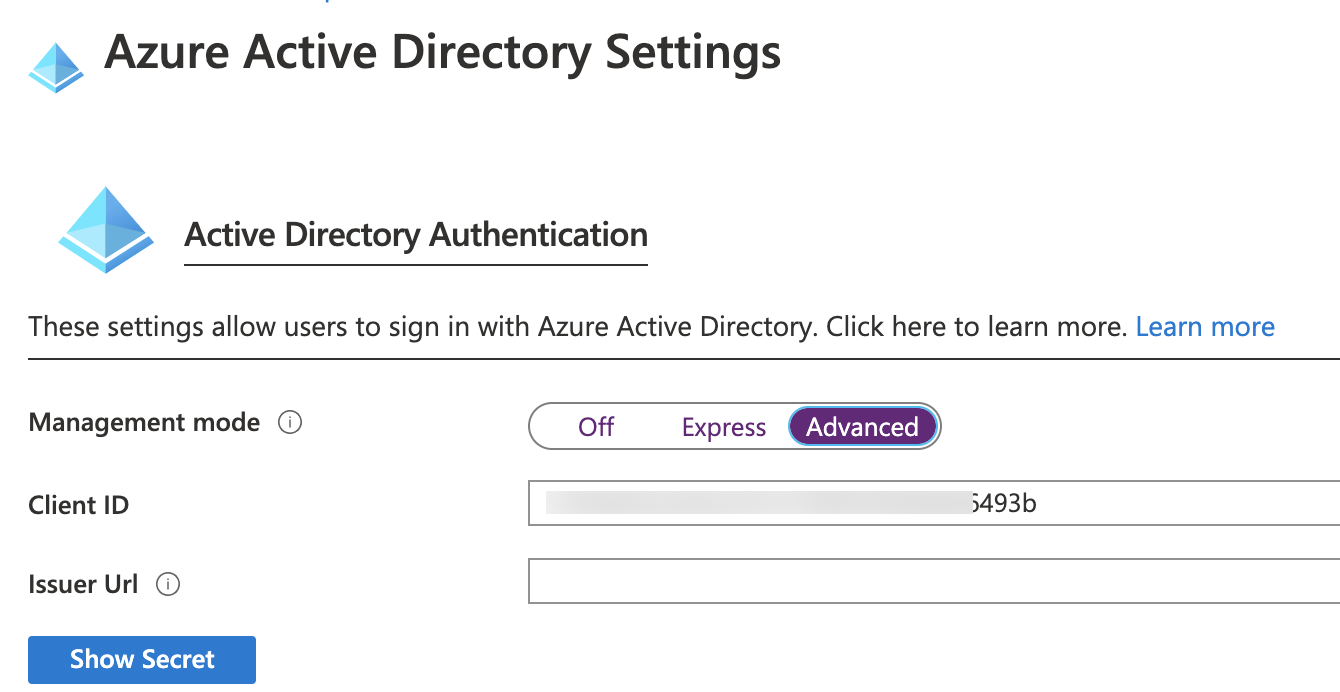
Impersonation within Azure Function or Custom Connector when using AAD authentication - Microsoft Dynamics 365 CRM Tips and Tricks
.png)