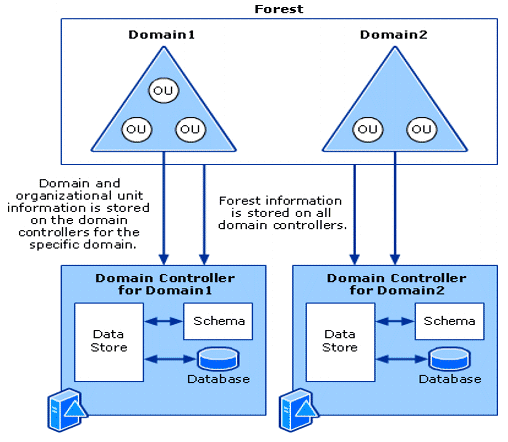
GitHub - Integration-IT/Active-Directory-Exploitation-Cheat-Sheet: A cheat sheet that contains common enumeration and attack methods for Windows Active Directory.
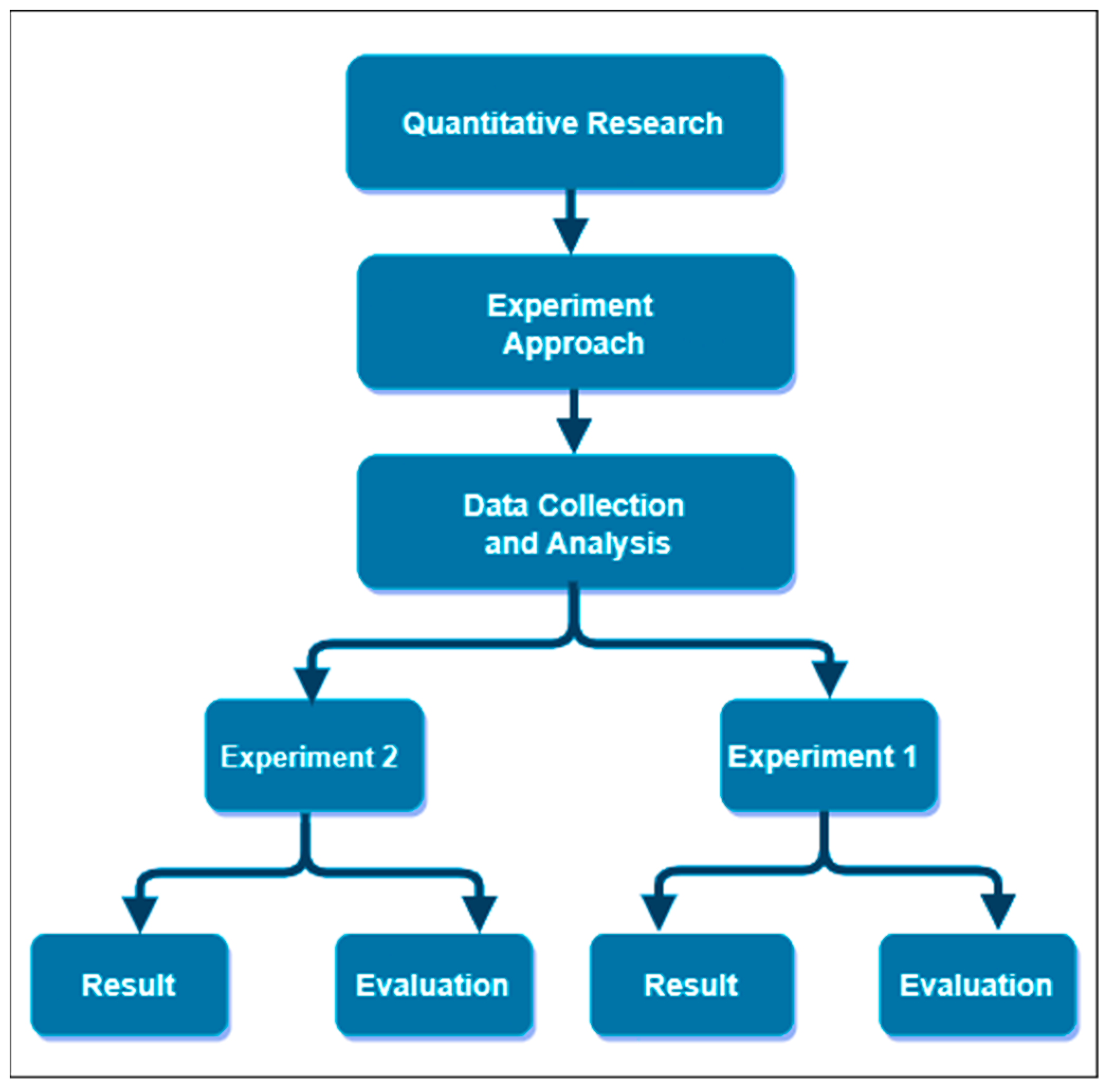
Future Internet | Free Full-Text | Exploiting Misconfiguration Vulnerabilities in Microsoft’s Azure Active Directory for Privilege Escalation Attacks