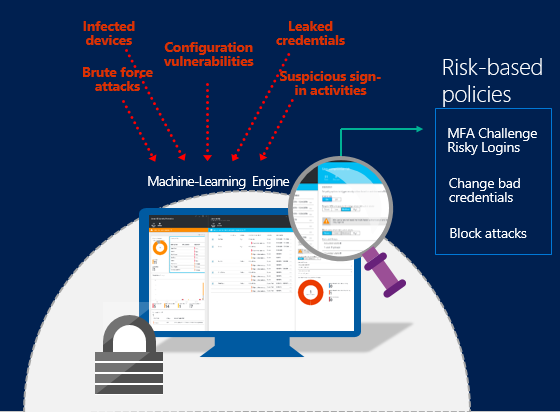
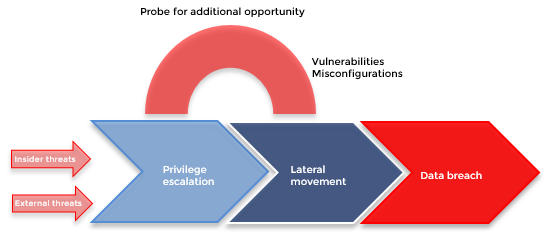
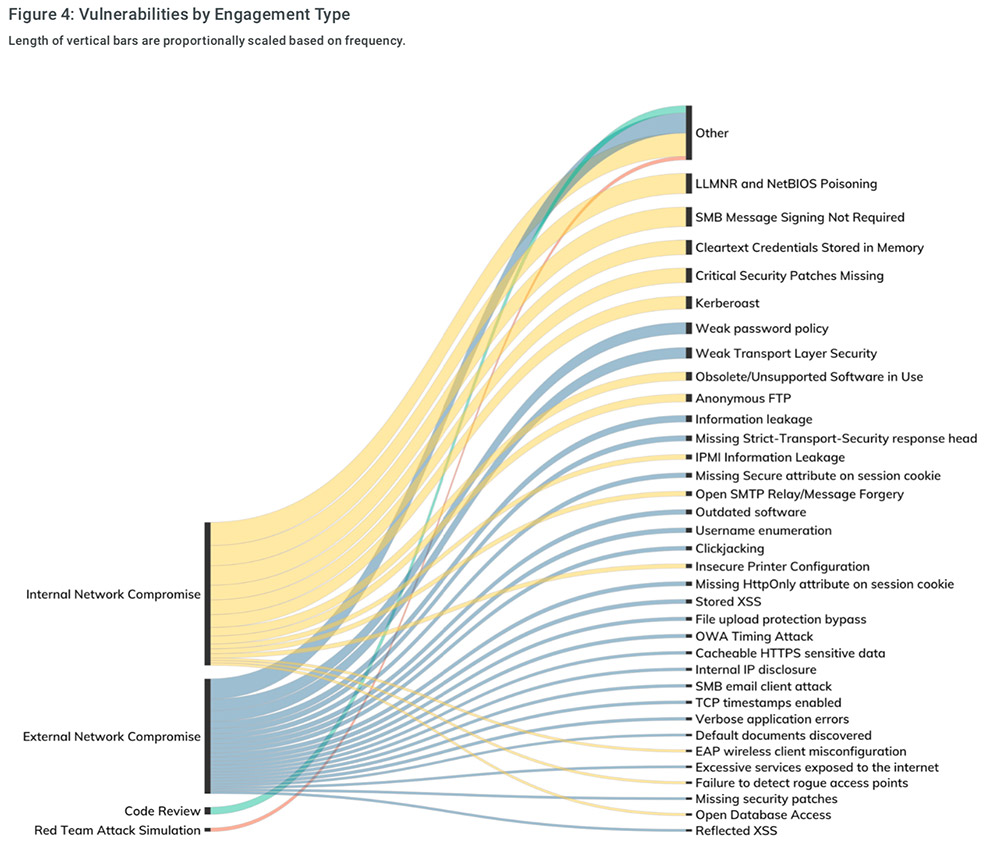
GitHub - infosecn1nja/AD-Attack-Defense: Attack and defend active directory using modern post exploitation adversary tradecraft activity

Top Legacy Active Directory Infrastructure Vulnerabilities and How Attackers See Them - Cyber Defense Magazine

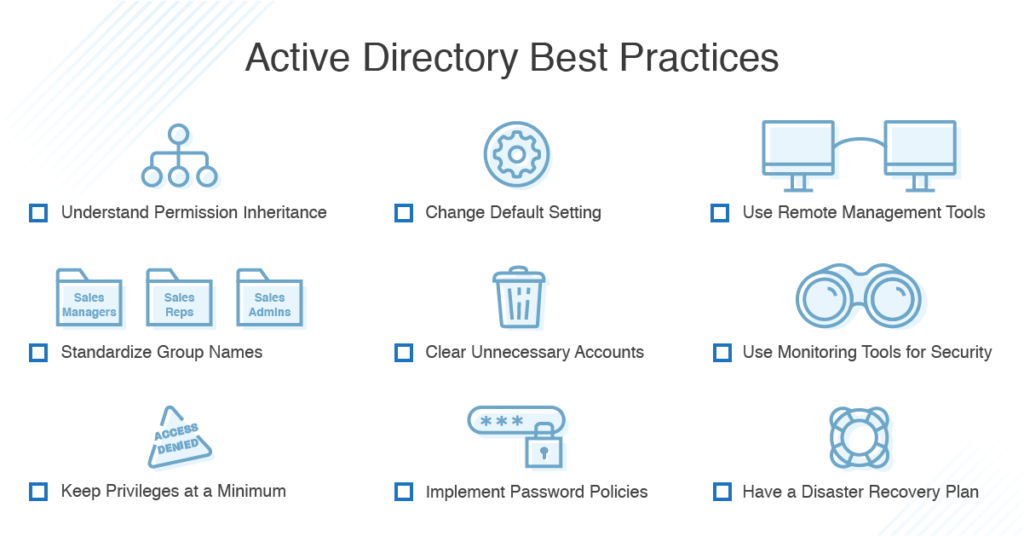
AD Attack Vectors: Top Active Directory Vulnerabilities eBook : Nafees, Muhammad, Arafat, Zahid, Ashraf, Nadeem: Amazon.in: Kindle Store

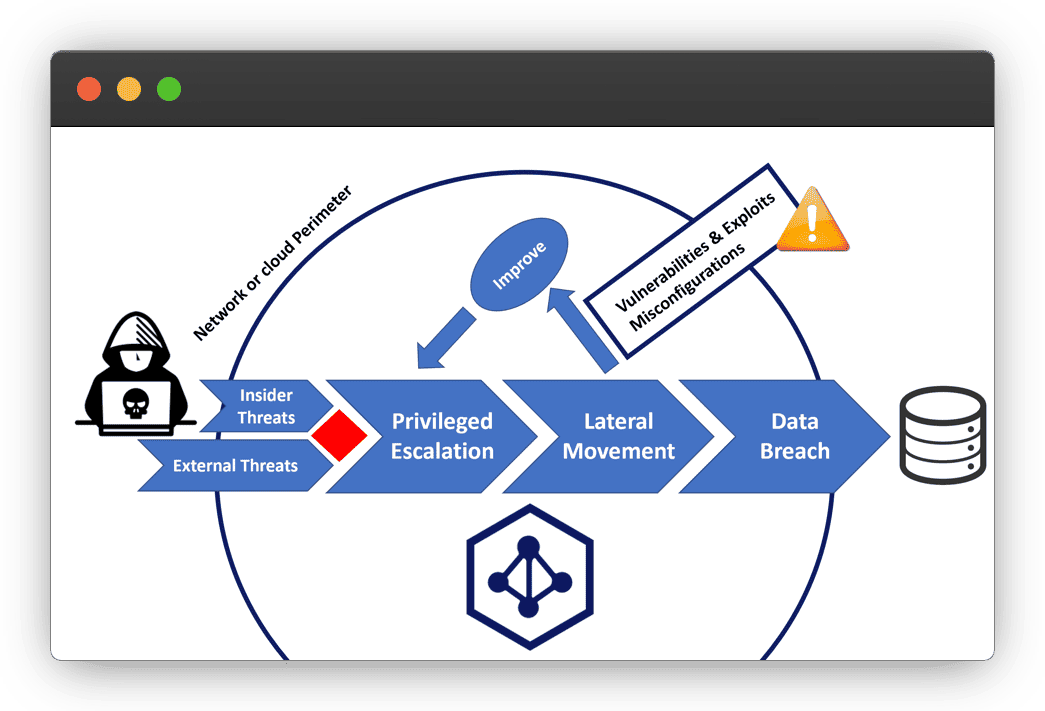
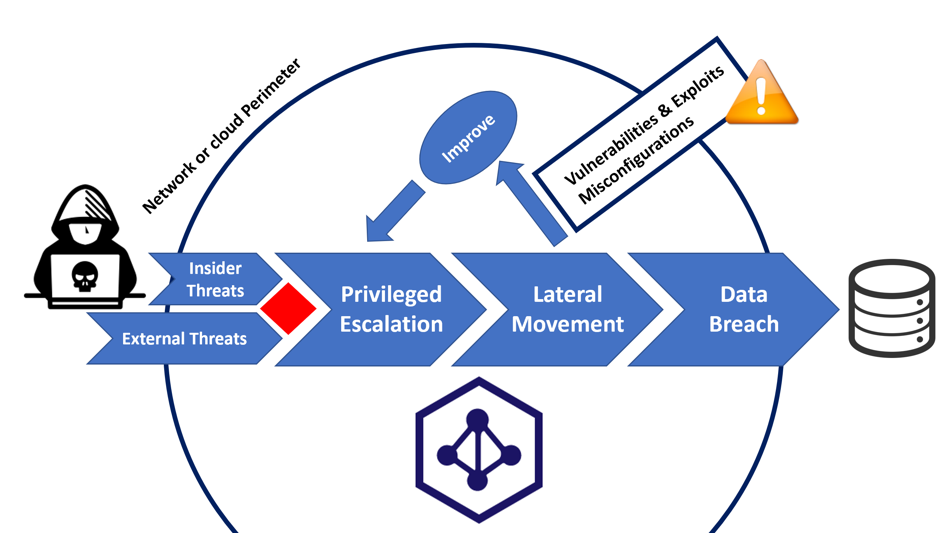
Future Internet | Free Full-Text | Exploiting Misconfiguration Vulnerabilities in Microsoft’s Azure Active Directory for Privilege Escalation Attacks