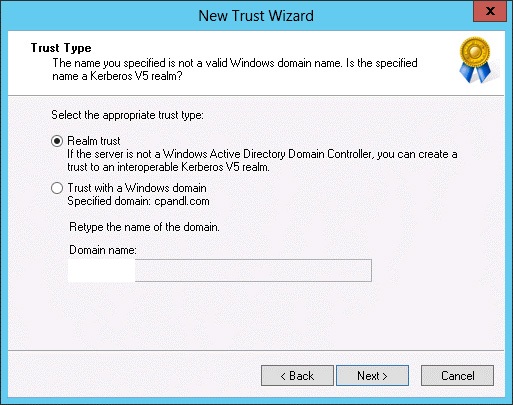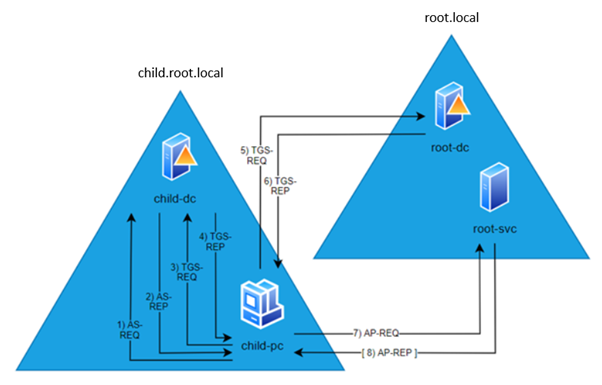
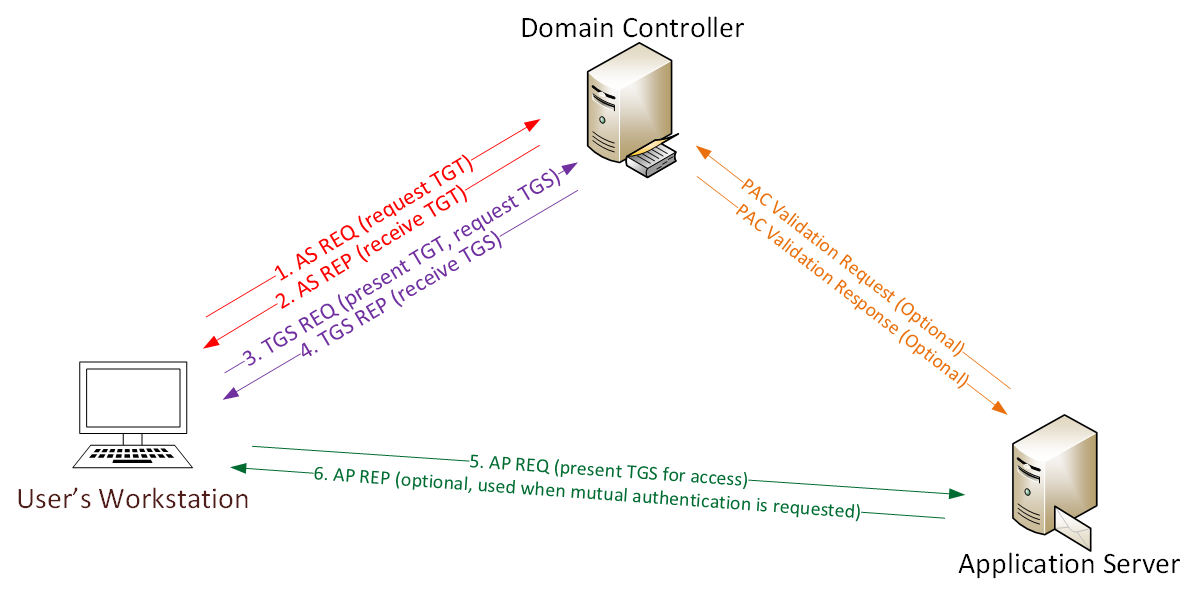
SID filter as security boundary between domains? (Part 1) - Kerberos authentication explained — Improsec | improving security
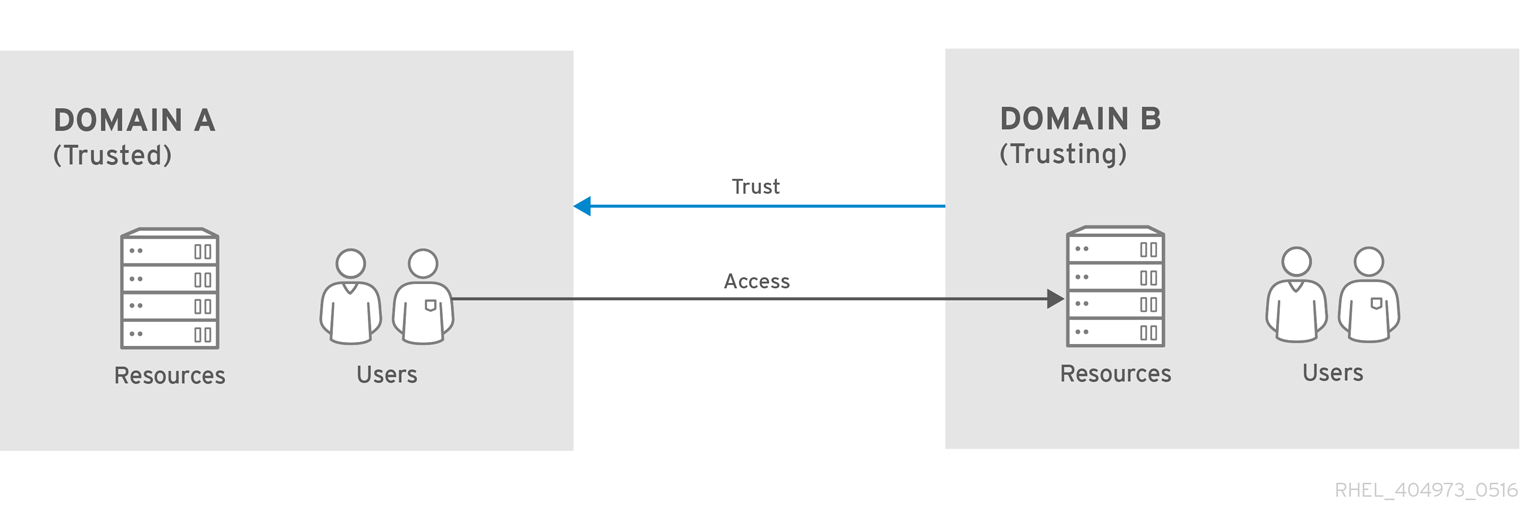
It's All About Trust – Forging Kerberos Trust Tickets to Spoof Access across Active Directory Trusts » Active Directory Security

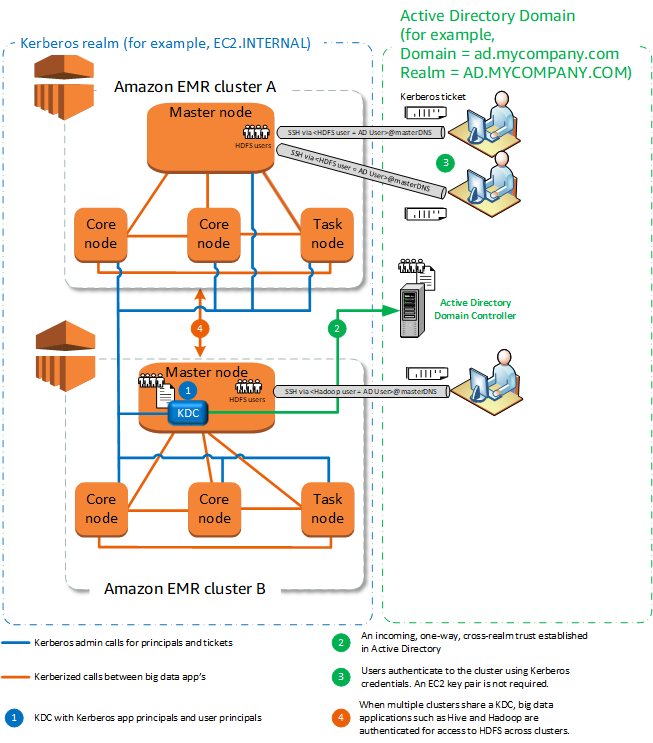
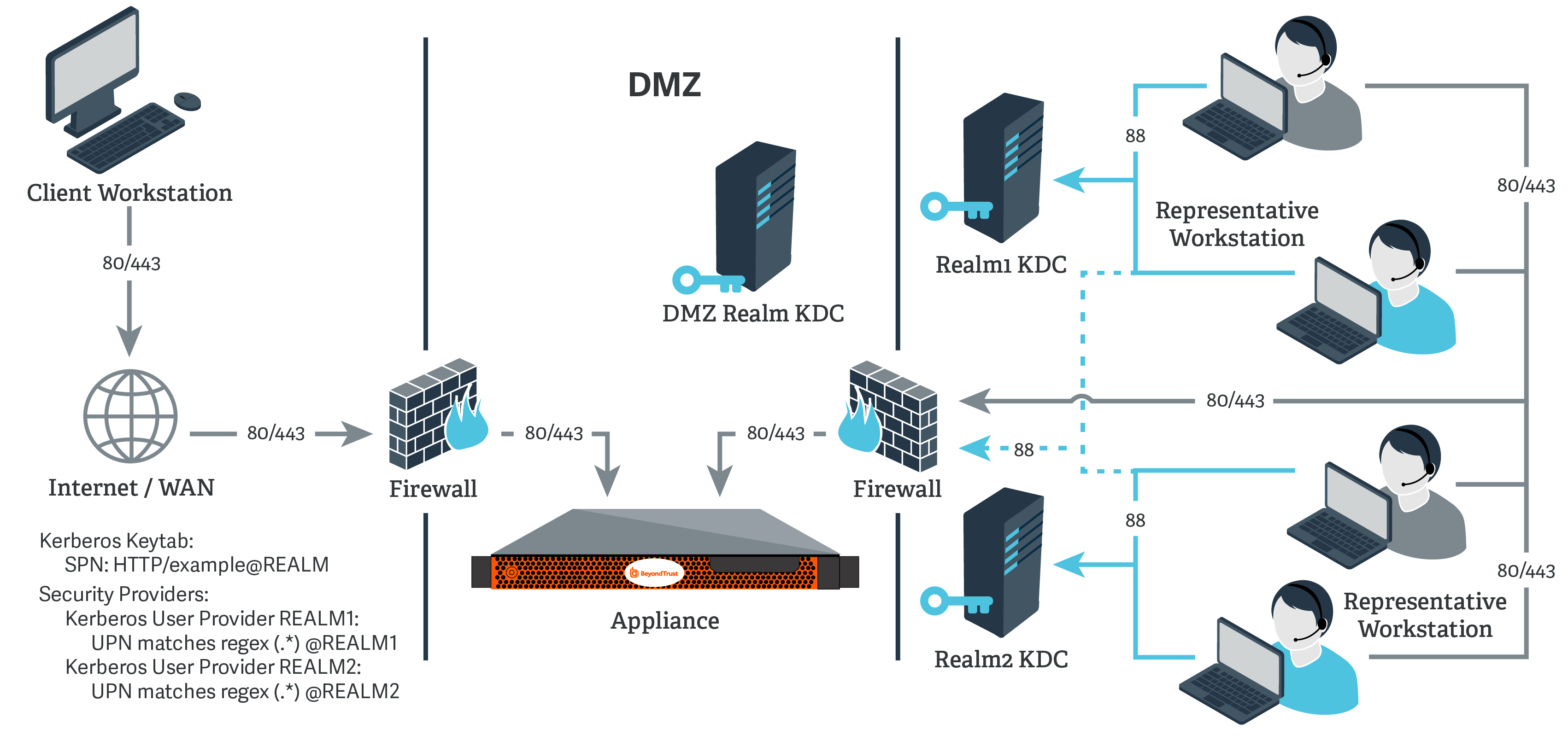
Deep dive into Amazon EMR Kerberos authentication integrated with Microsoft Active Directory | Noise